Cookies help us deliver our services. By using our services, you agree to our use of cookies.
Search
RSS
News
DDoS Extortion Attacks Against SIP/RTP VoIP Providers -Monday, November 1, 2021
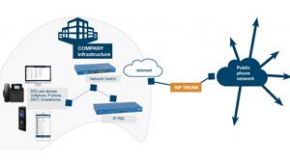
Beginning in September 2021, aggressive threat actors have targeted multiple Voice-over-IP (VoIP) communication providers with a campaign of high-impact DDoS extortion attacks. These attacks incorporate a range of UDP reflection/amplification and application-level DDoS attack vectors which have disrupted VoIP services for organizations unprepared to mitigate the attacks.
DNS Flag Day Feb 1, 2019 - We can Help ! -Wednesday, January 30, 2019
What is happening? The current DNS is unnecessarily slow and inefficient because of efforts to accommodate a few DNS systems that are not in compliance with DNS standards established two decades ago. To ensure further sustainability of the system it is time to end these accommodations and remediate the non-compliant systems. This change will make most DNS operations slightly more efficient, and also allow operators to deploy new functionality, including new mechanisms to protect against DDoS attacks.
RoboCallers What are They and How to Stop Them -Wednesday, January 23, 2019
We’ve all been there. You’re relaxing at home, minding your own business, when suddenly you receive a call from a number you don’t recognize. You let it ring a few times, unsure if you want to pick up, but eventually shrug and hit Accept. And instead of another human, you hear what appears to be a prerecorded message about something you likely don’t care about. In some cases, the message isn’t even prerecorded — it’s generated on-the-fly using text-to-speech technology.
Why Google is Forcing You To Have SSL Certificates on Your Websites -Wednesday, January 2, 2019
Welcome to 2019 "Google says". Don’t have an SSL Certificate? Google is going to flag your website this year! We turn to the internet for everything. From selling to buying, it is the introduction of an E-world. With this dominating trend, online security has become a necessity. Undoubtedly, Google loves its users and therefore, is coming up with every possible way to make us feel secure here on the internet. With its recent announcement, earlier this year, Google will flag all the unencrypted internet by the end of 2018.
ICT Client Area Login now offers you to use a Two-Factor Authentication login -Thursday, November 15, 2018
Our Client Area Login now offers you to use a Two-Factor Authentication login. TOTP requires that a user enter a 6 digit code that changes every 30 seconds to complete login. This works with mobile apps such as OATH Token and Google Authenticator.
How to Prevent Phishing Attacks -Thursday, November 15, 2018
A typical way of getting hacked is falling for a phishing attack. In fact, most of the large data breaches in recent years have been due to phishing.